Identity Protection
Like many SMBs, our customers are frequently contacted by overzealous IT salespeople telling them that their accounts are not secure. These salespeople often use leaked or pwned credentials – that is, email addresses and passwords that have been previously exposed in a data breach – to make their target believe they are under threat.
Luckily, most of our clients are aware of Retrac’s robust stance on identity security and simply reach out to us and make sure they aren’t at risk. That said, I thought it important to highlight some information about how our Complete Cloud identity security system works.
All our Complete Cloud (our main package for Microsoft 365) customers have Microsoft Identity Protection configured to ensure workplace identities are monitored and secure.
What exactly do we mean by monitored and secure?
Identity Protection uses learnings Microsoft has acquired from managing organisations’ accounts with Azure AD, the consumer space with Microsoft Accounts, and in gaming with Xbox to protect your users. Microsoft analyses 6.5 trillion signals per day to identify and protect customers from threats.
The signals are generated by, and fed to, Identity Protection, we then utilise Conditional Access to make access decisions or feedback to a security information or event management report for further investigation.
In a nutshell, Identity Protection is a tool that allows organizations to accomplish three key tasks:
- Automate the detection and remediation of identity-based risks.
- Investigate risks using data in the portal.
- Export risk detection data to third-party utilities for further analysis.
Each day, Microsoft’s machine learning and heuristic systems provide risk scores for 18 billion login attempts for over 800 million distinct accounts, 300 million of which are, for the majority, done by adversaries (entities like: criminal actors, hackers).
The top 3 attacks on Microsoft’s Identity Systems
Here are the recent volume statistics for these attacks:
- Breach replay: 4.6BN attacks detected in May 2018
- Password spray: 350k in April 2018
- Phishing: This is hard to quantify exactly, but Microsoft saw 23M risk events in March 2018, many of which are phish related.
Risk detection and remediation
Retrac have configured all the below Identity Protection classes to act in a way that we are confident your accounts are secure:
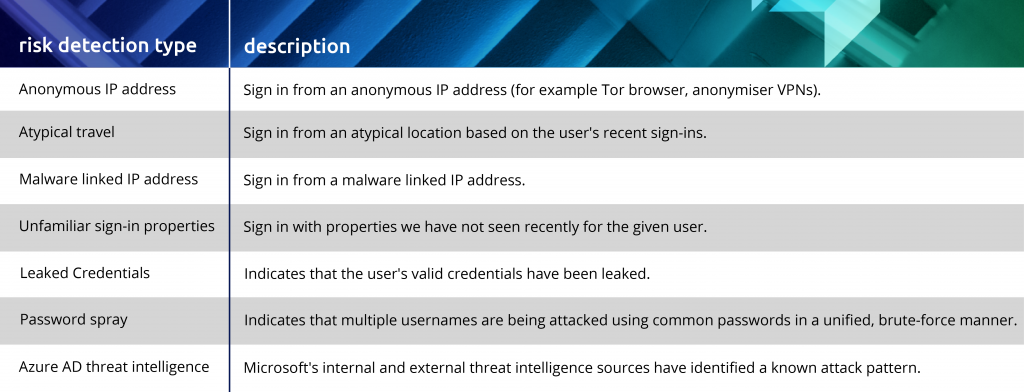
Most of the responses to the above risks are completely automated. The user will receive a Multifactor Authentication request and clear up the concern. We also receive a notification that this has happened. When a more sinister detection occurs, we have rules in place to block the sign–in until our administrators can review the incident and reset the account.
It’s important to note that we are protecting your Microsoft 365 work account, in fact, we spend all our efforts protecting your work account. The important message here is you should set up Single Sign–In to any other applications you use in your business to use the Microsoft work account to sign–in. Speak to us if you need help identifying any apps that should be included. Most work applications allow for this now and it means at no extra costs you can have the same robust security applied to those add on apps as well.
As for the sales folk reaching out to every business trying to tell you that your credentials have been leaked online, you can confidently inform them that Retrac has secured your logins and let us know. We will always review a third-party report and cross-check our efforts.
Contact our team to get started on your Complete Cloud journey.